Shell/Fingerprints: Unterschied zwischen den Versionen
imported>Burghardt |
imported>Burghardt |
||
| Zeile 5: | Zeile 5: | ||
== Current fingerprints as of October 2017 == |
== Current fingerprints as of October 2017 == |
||
| ⚫ | |||
| − | |||
| ⚫ | |||
<pre> |
<pre> |
||
| − | ~$ for F in /etc/dxs/shellX-ssh/*.pub ; do echo -e "\n$F:"; ssh-keygen -l -E |
+ | ~$ for F in /etc/dxs/shellX-ssh/*.pub ; do echo -e "\n$F:"; ssh-keygen -l -E sha256 -f $F; done |
/etc/dxs/shellX-ssh/ssh_host_ecdsa.pub: |
/etc/dxs/shellX-ssh/ssh_host_ecdsa.pub: |
||
| − | 256 |
+ | 256 SHA256:L+FCMj2bm8x/BfR8AdaaLnqTmFD35D0EYNlFG7a2dt8 root@nfsadm (ECDSA) |
/etc/dxs/shellX-ssh/ssh_host_ed25519_key.pub: |
/etc/dxs/shellX-ssh/ssh_host_ed25519_key.pub: |
||
| − | 256 |
+ | 256 SHA256:H4FLNG2aNYRZ3jxepIx5E0s0a2ZvtZbbmVLt56b+nK0 root@nfsadm (ED25519) |
/etc/dxs/shellX-ssh/ssh_host_rsa_key.pub: |
/etc/dxs/shellX-ssh/ssh_host_rsa_key.pub: |
||
| − | 2048 |
+ | 2048 SHA256:DpP5/EfbApVUwseVeQOVpAFvGiZIJmYmjUyC4Cnuatk root@nfsadm (RSA) |
</pre> |
</pre> |
||
| ⚫ | |||
| ⚫ | |||
<pre> |
<pre> |
||
| − | ~$ for F in /etc/dxs/shellX-ssh/*.pub ; do echo -e "\n$F:"; ssh-keygen -l -E |
+ | ~$ for F in /etc/dxs/shellX-ssh/*.pub ; do echo -e "\n$F:"; ssh-keygen -l -E md5 -f $F; done |
/etc/dxs/shellX-ssh/ssh_host_ecdsa.pub: |
/etc/dxs/shellX-ssh/ssh_host_ecdsa.pub: |
||
| − | 256 |
+ | 256 MD5:07:84:c9:e1:59:4f:03:75:69:b1:e4:d0:b4:1f:9a:cd root@nfsadm (ECDSA) |
/etc/dxs/shellX-ssh/ssh_host_ed25519_key.pub: |
/etc/dxs/shellX-ssh/ssh_host_ed25519_key.pub: |
||
| − | 256 |
+ | 256 MD5:93:11:29:c4:a2:03:e1:2d:b1:82:05:74:dd:a5:3b:9a root@nfsadm (ED25519) |
/etc/dxs/shellX-ssh/ssh_host_rsa_key.pub: |
/etc/dxs/shellX-ssh/ssh_host_rsa_key.pub: |
||
| − | 2048 |
+ | 2048 MD5:de:db:6e:72:52:de:30:73:db:bb:6e:79:df:f9:2c:0d root@nfsadm (RSA) |
</pre> |
</pre> |
||
| − | |||
| − | |||
== Actually compare a fingerprint when establishing a session == |
== Actually compare a fingerprint when establishing a session == |
||
Version vom 2. Oktober 2017, 14:27 Uhr
- Back to Shell
To verify a fingerprint you need to know the correct one. These to-be-verified correct fingerprints can be shown after you're logged in on the target server. Of course this is a classic chicken-and-egg problem situation. You need to get the correct fingerprints through an independent communication channel in beforehand. In our case that is the list below:
Current fingerprints as of October 2017
- sha256:
~$ for F in /etc/dxs/shellX-ssh/*.pub ; do echo -e "\n$F:"; ssh-keygen -l -E sha256 -f $F; done /etc/dxs/shellX-ssh/ssh_host_ecdsa.pub: 256 SHA256:L+FCMj2bm8x/BfR8AdaaLnqTmFD35D0EYNlFG7a2dt8 root@nfsadm (ECDSA) /etc/dxs/shellX-ssh/ssh_host_ed25519_key.pub: 256 SHA256:H4FLNG2aNYRZ3jxepIx5E0s0a2ZvtZbbmVLt56b+nK0 root@nfsadm (ED25519) /etc/dxs/shellX-ssh/ssh_host_rsa_key.pub: 2048 SHA256:DpP5/EfbApVUwseVeQOVpAFvGiZIJmYmjUyC4Cnuatk root@nfsadm (RSA)
- md5 is officially deprecated but better than nothing:
~$ for F in /etc/dxs/shellX-ssh/*.pub ; do echo -e "\n$F:"; ssh-keygen -l -E md5 -f $F; done /etc/dxs/shellX-ssh/ssh_host_ecdsa.pub: 256 MD5:07:84:c9:e1:59:4f:03:75:69:b1:e4:d0:b4:1f:9a:cd root@nfsadm (ECDSA) /etc/dxs/shellX-ssh/ssh_host_ed25519_key.pub: 256 MD5:93:11:29:c4:a2:03:e1:2d:b1:82:05:74:dd:a5:3b:9a root@nfsadm (ED25519) /etc/dxs/shellX-ssh/ssh_host_rsa_key.pub: 2048 MD5:de:db:6e:72:52:de:30:73:db:bb:6e:79:df:f9:2c:0d root@nfsadm (RSA)
Actually compare a fingerprint when establishing a session
Older implementations (for example from debian Jessie) use md5 - without explicitly stating this fact:
~$ ssh -o VisualHostKey=yes shell.informatik.uni-goettingen.de The authenticity of host 'shell.informatik.uni-goettingen.de (134.76.81.100)' can't be established. ECDSA key fingerprint is 07:84:c9:e1:59:4f:03:75:69:b1:e4:d0:b4:1f:9a:cd. +---[ECDSA 256]---+ | ..++o=o=o | | .++ o *+o | | o . ..+ . | | . * . | | S . o E | | . | | | | | | | +-----------------+
Newer version (e.g. from Ubuntu Xenial) use sha256 by default:
~$ ssh -o VisualHostKey=yes shell.informatik.uni-goettingen.de The authenticity of host 'shell.informatik.uni-goettingen.de (134.76.81.100)' can't be established. ECDSA key fingerprint is SHA256:L+FCMj2bm8x/BfR8AdaaLnqTmFD35D0EYNlFG7a2dt8. +---[ECDSA 256]---+ | o+o== | | .o.o.o+ | | . o ++. | | . . o *.o. | | o +.S. * +o .| | +.= o. =.o.o| | +.o+.+ .E| | o ++.= | | =..o . | +----[SHA256]-----+
On those newer ssh-clients you can request a specific algorithm to be used:
~$ ssh -o VisualHostKey=yes -o FingerprintHash=md5 shell.informatik.uni-goettingen.deHost key fingerprint is MD5:07:84:c9:e1:59:4f:03:75:69:b1:e4:d0:b4:1f:9a:cd +---[ECDSA 256]---+ | ..++o=o=o | | .++ o *+o | | o . ..+ . | | . * . | | S . o E | | . | | | | | | | +------[MD5]------+
Note that older implementations just don't know "-o FingerprintHash" and will generate an error message only. That's the reason we list both old and new fingerprints above...
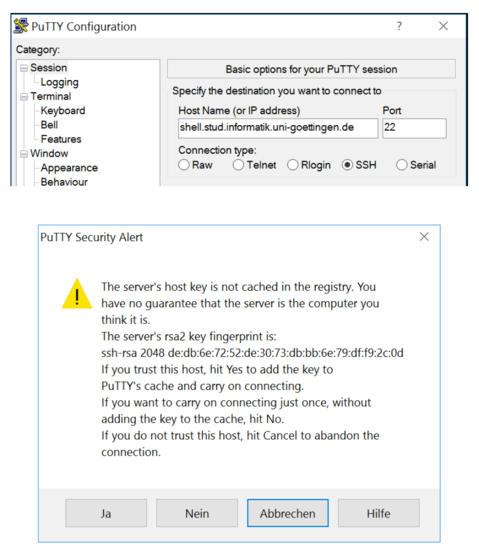
Windows
PuTTY on windows looks like this: